The Tinba virus, also known as the Tiny Banker Trojan, is a powerful banking malware that silently steals private financial data from victims via emails and downloaded files. Tinba Trojan’s primary objective is to steal the user’s financial data during online banking transactions.
Tiny Banker Trojan Tinba continues to be an ongoing issue for cybersecurity professionals, highlighting the critical need for solid security measures in today’s digital world.
In this article, we will explain the treatment and how to prevent the spread of Tinba virus:
What Is Tinba Virus?
A major threat to online banking systems is Tinba, an intelligent and destructive financial virus also known as “Tiny Banker” or “Tiny Banker Trojan.”
Its purpose is to steal sensitive financial data from its victims, including credit card numbers, login credentials, and other personal information.
It usually targets Windows-based computers and spreads via drive-by downloads, malicious websites, and spam emails.
How Tiny Banker Trojan Tinba Works?
Tinba, sometimes referred to as the Tiny Banker Trojan, uses cunning and stealth to carry out its malevolent actions. This is how it usually operates:
There are several ways that Tinba can propagate, including hacked websites, malicious downloads, and spam emails.
By mistake, a user downloads and runs the malware, giving Tinba access to the victim’s computer.
1. Setup:
Tinba hides its presence and avoids being discovered by security software by installing itself as a rootkit once it has gained access to the victim’s computer.
2. Browser Attack:
Tinba, the Tiny Banker Trojan, is made especially for Internet banking platforms. When the victim visits a banking website, the malware subtly inserts malicious code into the page, changing its look and functionality without the user’s knowledge.
3. Stealing sensitive Information:
Sensitive financial data, such as account numbers, credit card numbers, login passwords, and personal identification information, is the precise target of Tinba.
As the user enters this information on the fraudulent banking page, it is collected in real-time.
4. User Data Capture:
Tinba secretly logs all user activity, including keystrokes, mouse clicks, and login credentials, while the victim uses the compromised banking website.
5. Communication with the Server:
Tinba periodically exchanges data with an attacker-managed remote command-and-control server.
The stolen data is transmitted to this server, which acts as the main archive for all the compromised data.
6. Transaction Manipulation:
Under certain circumstances, Tinba has the ability to alter or intercept online transactions, rerouting money to the attacker’s account or changing transaction details without the user’s awareness.
7. Tinba Escape Methods:
Tinba uses a variety of evasion strategies to elude detection and elimination, including encrypting its communications with the C&C server, frequently altering its code, and modifying its behaviour to get around security and antivirus programs.
Overall, Tinba is a very dangerous and dynamic banking Trojan that seriously endangers users of online banking.
Experts in cybersecurity are constantly faced with this challenge because of its ability to operate stealthily and pilfer confidential financial data.
It emphasizes how crucial it is to have strong security procedures in place to guard against threats like malware.
How to Remove Tinba Trojan, Follow These Steps
To guarantee total eradication from the compromised system, treatment, and elimination of the Tinba Trojan requires a systematic and vigilant approach.
The general procedures for handling the Tinba Trojan are as follows:
1. Isolate the Infected System:
If you suspect a system has been infected with Tiny Banker Trojan Tinba, disconnect it from the network immediately.
This stops the malware from contacting its command-and-control server and spreading to other devices.
2. Use Reliable Antivirus Software:
Use trustworthy, up-to-date antivirus or anti-malware software to fully inspect the compromised system.
Tinba and its associated components ought to be detectable and removable by the antivirus program.
You can choose Malwarebytes, Norton, Avira, or any other malware program to scan your PC.
3. Delete Infected Files:
When the antivirus program detects the Tinba Trojan and any related malicious files, do as instructed by the program to quarantine and remove the files.
Keep a watchful eye out for any potentially compromised system files and permit the antivirus program to replace or repair them as necessary.
4. Update Operating System and Software:
Make sure that the impacted system’s web browsers, operating system, and other applications are all up to date with the most recent security patches.
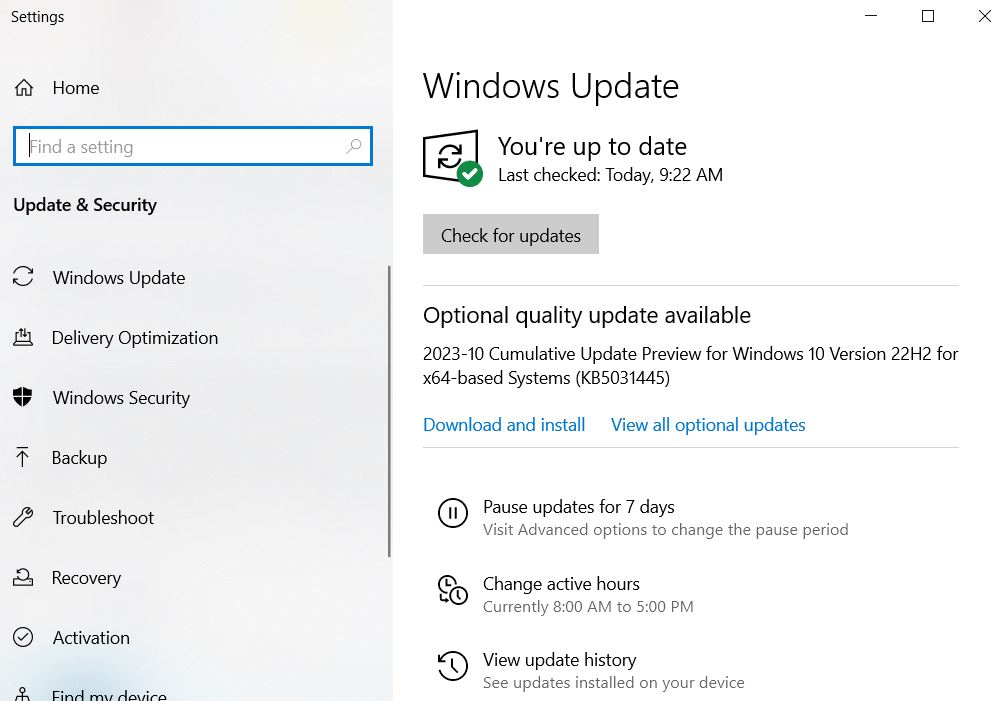
This can aid in stopping new infections by utilizing known vulnerabilities.
5. Change Passwords:
After the removal process, it’s crucial to change the passwords for all online accounts, particularly those related to banking and financial services, as Tinba steals login credentials.
Select robust and distinct passwords for every account to improve protection against the Tiny Banker Trojan.
6. Seek Professional Help:
Consider getting assistance from a team of IT support specialists or professional cybersecurity experts if the infection is severe or the removal process is beyond your area of expertise.
Tiny Banker Trojans are now a problem for most IT consulting teams.
7. Manual Removal Using Safe Mode:
For everyday computer users, a manual removal guide might be too complex. It may take hours to finish and requires advanced IT knowledge to be done correctly, it could compromise Windows completely.
For everyday computer users, a manual removal guide might be too complex. It may take hours to finish and requires advanced IT knowledge to be done correctly, it could compromise Windows completely.
Step 1. Access Safe Mode with Networking:
- It is recommended to remove malware manually in Safe Mode.
- Press Start, then select “Restart” your PC.
- As soon as your computer turns on, begin tapping the F8 button repeatedly until the Advanced Boot Options window appears (if that doesn’t work, try F2, F12, Del, etc.;).
- From the list, choose Safe Mode with Networking.
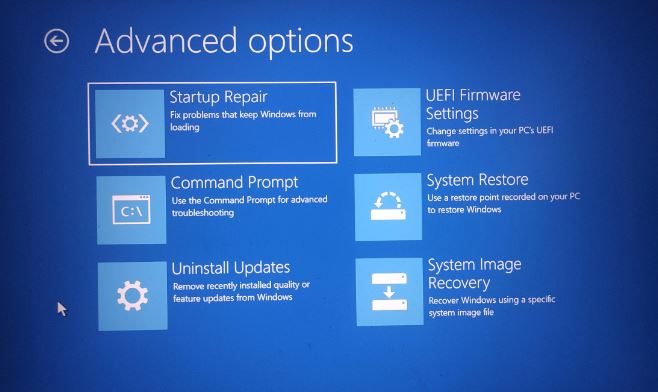
Windows 10 / Windows 8:
- Select Settings with a right-click on the Start button.
- To select Update & Security, scroll down.
- From the left menu, choose Recovery.
- To access the Advanced Startup section, scroll down.
- Now click Restart.
- Click on Troubleshoot.
- Access the Advanced menu.
- Choose Startup Preferences.
- Click “Restart.”
- To enable safe mode with networking, press or click 5.
Step 2. Shut down suspicious processes:
Windows Task Manager is a helpful utility that displays every background process. You must terminate any processes that malware may be executing:
- To access Windows Task Manager, use the keyboard shortcuts Ctrl + Shift + Esc.
- Select “More information.”
- Examine anything questionable in the Background Processes section by scrolling down.
- Use the right-click menu to open the file location.
- Return to the process, and select End Task with a right-click.
- Empty the malicious folder’s contents.
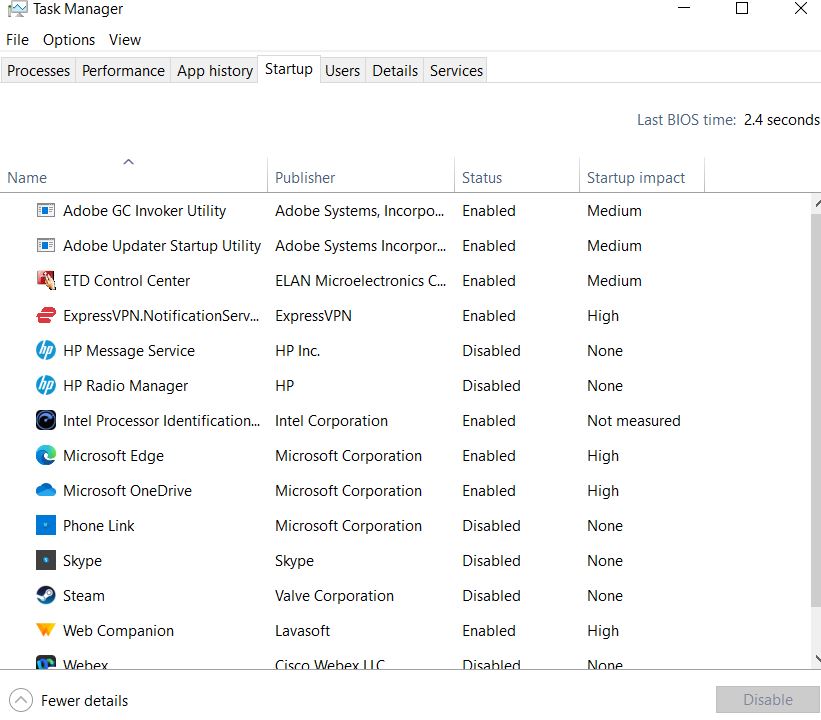
Step 3. Check Program Startup:
- To access Windows Task Manager, use the keyboard shortcuts Ctrl + Shift + Esc.
- Select the tab for Startup.
- To disable the suspicious program, right-click on it and select Disable.
Step 4. Delete Virus Files:
There are files on your computer that are connected to malware in different locations. The following guidelines may assist you in locating them:
- In Windows Search, type “Disk Cleanup” and hit Enter.
- Choose the drive that needs to be cleaned (by default, C: is your main drive and is probably the one that contains malicious files).
- To remove the list, scroll through the files and choose the following:
- Downloads of Temporary Internet Files
- Recycle Bin
- Temporary files
- Select System file cleanup.
Additionally, you can search for additional malicious files concealed in the following folders by typing these names into Windows Search and then pressing “Enter”
- %ProgramData%
- %AppData%
- %LocalAppData
- % %WinDir%
- Restart the computer in standard mode once you are done.
Conclusion
Tinba Trojan, Adware, spyware, Trojans, and other programs endanger our privacy. By following the steps shown in this guide, you can easily get rid of the Tinba Trojan virus. If you have any method to share with us, leave that in the comment section below.

It’s me Mosaab, the founder and leading author of MalwareYeti.com. Over the years, I have gained a lot of experience when it comes down to building or fixing computers. Throughout my journey, I’ve built gaming PCs, fixed irritating Windows errors, and removed sticky malware/viruses that have affected machines. You can learn more about me on our About us page.