Our daily challenges are formidable due to the constantly changing cybersecurity landscape. The threat posed by crypto-malware is among the most notable risks.
Stats that should worry you indicate that the use of crypto-malware in cybercrime has grown.
Then, what is exactly crypto malware? Crypto malware is a crafty type of software that takes advantage of computer processing power and other devices’ resources to plunder virtual currencies.
Cyberjacking is a technique that malware uses to obtain assets in digital currency. Computers that have been stolen are usually used for cryptocurrency mining.
For instance, Monero is famous for his creative methods of disguising information so that other users can’t easily identify the person mining it.
As the world of digital finance continues to evolve, the emergence of cryptocurrencies has altered our perception of and behaviour toward money.
All the same, as cryptocurrencies gain popularity, more malware associated with them is drawn to major players like Bitcoin, Ethereum, and Litecoin.
The intricate patterns, preventative measures, trends, and historical development of this emerging threat will all be covered in detail in this article.
The Evolution of Cryptocurrency Malware
The process of creating cryptocurrency malware is complex and diverse, and both technology advancements and the changing nature of the digital economy have impacted it.
One of the earliest forms of cryptocurrency malware was the infamous Coinhive, a JavaScript miner that exploited website visitors’ computational resources to mine Monero.
This resulted in a new age of cybercrime, allowing hackers to profit online by exploiting the vulnerability of unsuspecting victims.
As more people wanted to use cryptocurrencies, malware got better and harder to detect.
Why Crypto-Malware Attacks Are Increasing?
Cybercriminals are using crypto-malware assaults more frequently as a result of the rising value and increased use of cryptocurrencies.
Once crypto-malware is installed on a victim’s device, it can typically operate autonomously and forever.
Attackers can thus anticipate a consistent profit from crypto-malware as long as the code is not discovered.
We anticipate seeing a rise in crypto-malware attacks shortly due to the constant creation of new cryptocurrency variants and the ongoing circulating of new variants of the malware.
How Does Crypto-Malware Work?
Unlike typical malware, crypto-malware does not aim to steal data. Instead, it makes use of the victim’s system to mine bitcoins for as long as possible, keeping it discreet and going on for a while.
Crypto-malware is a silent threat that, once downloaded, inserts harmful code into different programs and apps under the pretence of genuine software.

While the victim is using their smartphone, this malware will continuously mine for money in the background while they are using their phone.
The use of a hacked advertisement or website is a sophisticated technique of infection.
The victim’s device launches the script as soon as they go to the malicious website. It is the browser that contains the malicious code, not the computer itself.
Cryptojacking:
One of the most prevalent types of cryptocurrency malware is the unlawful mining of cryptocurrencies on a computer or other device.
Cryptojacking has changed the way malware is distributed, including through phishing and extortion.
Alternatively, they can surreptitiously insert mining scripts into webpages, mobile applications, and even advertisements to leverage the processing power of multiple devices without the owners’ knowledge.
This pervasive tendency has penetrated the digital ecosystem, impacting individuals, businesses, and even governmental entities.
Crypto-Malware Attacks vs Ransomware Attacks
Ransomware and crypto-malware attacks are both intended to bring in money for the perpetrator.
But there are big differences in how this is done. The data of a victim of a ransomware attack is encrypted until the attacker is paid.
If the payment is not received, the ransomware attackers might try to recoup their costs by selling the data on the dark web.
With an average ransom payment of millions in 2022, ransomware continues to be one of the most lucrative strategies used by cybercriminals.
Conversely, crypto-malware functions covertly and noiselessly in the background of the user’s system.
A crypto-malware attacker seeks to mine cryptocurrency on the victim’s device by hiding the malicious code for as long as possible, unlike a ransomware attack that demands payment in advance.
Impact of a Crypto-Malware Attack
Compared to ransomware attacks, massive data breaches, disruptive viruses, or Trojan horses, crypto-malware is less dangerous because it doesn’t explicitly steal data.
Still, it uses the victim’s computer resources to mine cryptocurrency, which is very taxing and hurts the user’s productivity.
The victim is likely to experience noticeably slower system processing speeds and may experience difficulty multitasking.
With plenty of illegal tools and services intended to aid in cybercrime, the dark web has developed into a haven for the distribution and sale of malware intended to steal cryptocurrency.
Dark web markets give hackers a place to purchase and trade malware, exploit kits, and botnets, allowing them to quickly and easily launch complex attacks.
Additionally, it is difficult for law enforcement organizations to find and capture people involved in the illegal trade of cryptocurrency malware due to the anonymity and encryption features of the dark web.
Symptoms of Crypto-Malware Infection
Cryptovirus infections can show up in a variety of ways, from the blatantly obvious to the surprisingly subtle.
Here is a summary of some of the most obvious indicators that you may have crypto malware on your computer:
1. Increased CPU Usage:
The processor or (CPU) of a computer is often the target of crypto-malware. The central processing unit (CPU) is the main processing component that manages the hardware, operating system, and applications of a computer.
It processes instructions from multiple components using intricate electronic circuitry. Therefore, an unusual spike in CPU usage is frequently observed on computers that are infected with crypto-mining malware.
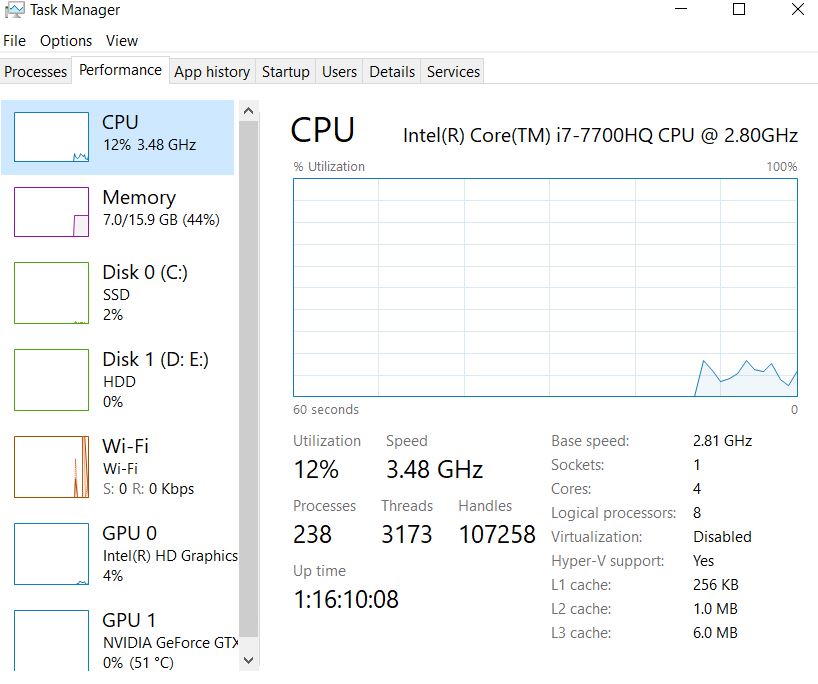
Task Manager on Windows and Activity Monitor on macOS can be used to track CPU activity.
A sudden and persistent increase in CPU utilization, especially while the system is not in use, maybe a sign of crypto malware infection.
2. Slow Performance:
The significant decrease in system performance that crypto-malware causes is frequently caused by its heavy reliance on CPU resources.
Because cryptocurrency mining operations are overloading the CPU, performance problems can be attributed to this.
When there is a crypto-malware infection, performance usually suffers as a result of secondary problems such as overheating, which sometimes forces the computer’s cooling system to work harder to alleviate the heat.
This frequently occurs at the same time as rising power bills.
3. Unusual Network Activity:
Unusual computer network behaviour may signal a potential crypto-malware infection.
This type of malware often communicates with external servers to receive updates and commands, leading to irregular network activity like frequent outgoing connections.
Additionally, unfamiliar processes or applications that consume more CPU resources than usual may also indicate a malware infection.
Regulatory and Legal Implications
Because cryptocurrency malware is so common, there have been legal and regulatory measures taken to try to lessen its effects and discourage bad actors.
To stop illegal activity, governments and regulatory agencies have implemented steps to improve cybersecurity standards, impose harsher penalties for cybercrime, and control cryptocurrency use.
In addition, law enforcement organizations have worked with foreign partners to break up cybercrime networks and stop the illegal sale of cryptocurrency malware,
which has resulted in the arrest and prosecution of those responsible for such things.
Mitigation Strategies and Best Practices
Because cryptocurrency malware is so widespread, people and organizations need to implement strong mitigation techniques and best practices to protect themselves from potential threats.
Yes, of course! The following are some safeguards against malware targeting cryptocurrency:
1. Use Reputable Wallets and Exchanges:
Select cryptocurrency exchanges and wallets that have a solid reputation for security and dependability.
Examine and pick platforms that have strong security features like cold storage for funds, multi-factor authentication (MFA), and frequent security audits.
2. Keep Software Updated:
Make sure you have the most recent security patches and updates installed on your operating system, antivirus program, web browsers, and Bitcoin wallets.
Install security updates often to defend against known flaws and exploits.
3. Exercise Caution with Links and Downloads:
Be cautious when responding to unsolicited emails, messages on social media, and ads that promote cryptocurrency investments or offers.
To prevent malware from stealing your cryptocurrency or personal information, stay away from clicking on dubious links and downloading attachments from unidentified sources.
4. Enable Two-Factor Authentication (2FA):
By turning on two-factor authentication (2FA), you can increase the security of your cryptocurrency wallets and accounts.
Employ authentication techniques to provide an additional degree of security against unwanted access, such as hardware tokens, authenticator apps, or SMS codes.
5. Implement Strong Password Practices:
For your wallets and cryptocurrency accounts, use strong, one-of-a-kind passwords. Avoid using passwords that are simple to figure out or using the same password for many accounts.
If you want to safely create and keep complicated passwords for your accounts connected to cryptocurrencies, think about utilizing a password manager.
6. Verify Website URLs and SSL Certificates:
Check the URL for errors or inconsistencies to ensure the website is legitimate before entering sensitive information or making cryptocurrency transactions online.
If you want to be sure that your connection is safe from malicious actors and cannot be intercepted, look for HTTPS encryption and active SSL certificates.
7. Practice Cold Storage for Long-Term Holdings:
To defend against online dangers like malware and hacking, think about keeping sizable quantities of cryptocurrency in hardware wallets or offline wallets, commonly referred to as cold storage.
Cybercriminals can hardly ever remotely access your funds thanks to cold storage solutions that keep your private keys offline.
8. Educate Yourself About Scams and Risks:
By routinely reading reliable sources of information and keeping up with industry news and developments, you can stay informed about common cryptocurrency scams and malware threats.
To prevent becoming a victim of dishonest schemes, familiarize yourself with the warning indicators and red flags of possible scams.
9. Backup Your Data and Wallets:
Back up your crucial data and cryptocurrency wallets regularly to safe places like encrypted cloud services or external hard drives.
Possessing backup copies of your wallets and data guarantees that you can retrieve your belongings and data in the case of a hardware malfunction or malware infection.
10. Exercise Skepticism and Due Diligence:
When it comes to cryptocurrency investments, deals, or opportunities that look too good to be true, proceed with caution and scepticism.
Before making an investment or disclosing sensitive information, do extensive research, confirm the legitimacy of the projects and the people involved, and consult with reliable sources for advice.
Future of Cryptocurrency Malware
The methods and plans used by bad actors to take advantage of this emerging market will change along with the cryptocurrency landscape.
Learn more about the cyber threat landscape.
It is probable that in the future, malware targeting cryptocurrencies will take on increasingly complex and devious forms,
employing cutting-edge methods like artificial intelligence and machine learning to avoid detection.
Additionally, by using transparent and unchangeable threat detection techniques, blockchain integration into cybersecurity could strengthen defences against cryptocurrency malware.
Conclusion
The dynamic and constantly evolving nature of cybersecurity threats in the digital age is reflected in the trends and patterns of malware targeting cryptocurrencies.
The emergence of cryptocurrency malware highlights the necessity of taking preventative action to lessen its effects, both in terms of how cryptojacking has evolved and how it affects people and businesses.
We can better prepare ourselves to navigate the challenging field of cybersecurity and protect the future of digital economies by comprehending the fundamental mechanisms and ramifications of cryptocurrency malware.

It’s me Mosaab, the founder and leading author of MalwareYeti.com. Over the years, I have gained a lot of experience when it comes down to building or fixing computers. Throughout my journey, I’ve built gaming PCs, fixed irritating Windows errors, and removed sticky malware/viruses that have affected machines. You can learn more about me on our About us page.

