The Malicious virus known as Trojan:Win32/Bamital.G is a kind that looks harmless but secretly contains dangerous code.
These Trojans can carry out several destructive tasks once they get inside the system, such as stealing confidential data, gaining control of it, and infecting additional devices with malware.
Trojans such as Trojan:Win32/Bamital.G are designed to steal sensitive data such as usernames, passwords, credit card numbers, and other personal information.
When it’s installed, the malware can access and record the user’s keystrokes, take screenshots, and even record audio and video.
This information can then be used for identity theft, financial fraud, and other nefarious purposes.
Trojan:Win32/Bamital.G is a dangerous piece of malware that allows hackers to remotely control a device, granting them access to sensitive information and allowing them to carry out malicious activities.
Moreover, once installed, the attacker has access to modify files, delete or encrypt data, and even control a device’s camera and microphone.
Furthermore, Trojans can be used to create a network of infected devices known as botnets, which can then be used for additional attacks.
If you suspect that your device has been infected with this malware, you must act quickly to prevent further damage.
How Trojan:Win32/Bamital.G Virus Affects Your Computer?
- Viruses can be installed by clicking on dubious links in spam emails.
- Malware infections can also arise from free hosting resources that are accessible online.
- Viruses can be installed covertly alongside other programs, particularly shareware or freeware programs.
- You run a higher risk of contracting a virus if you use illicit peer-to-peer (P2P) resources to download pirated software.
So, before you begin the manual removal process, follow these steps:
Google Chrome:
- To access the Menu button, move to the top right corner of the screen and click the three dots there.
- Choose “Settings” to select “Advanced”.
- Scroll down to the “Privacy and Security” section, and then choose “Content settings” and finally “Notification.”
- Locate every dubious URL. Select “Remove” or “Block” by clicking the three dots on the right.
Mozilla Firefox:
- Click on the main menu with three dots in the upper right corner of the screen.
- Choose “Privacy and Security” from the toolbar located on the left side of the screen after selecting “Options.”
- Proceed to the “Permission” section by slowly scrolling down, then select “Settings” from the menu next to “Notifications.”
- Choose each of the dubious URLs in the window that just popped up. Choose “Block” from the drop-down menu by clicking on it.
Internet Explorer:
- Click the Gear button in the right corner of the Internet Explorer window.
- Select “Internet Options.”
- Choose the “Privacy” tab, followed by “Settings” in the “Pop-up Blocker” section.
- One by one, pick each questionable URL, then select “Remove.”
Microsoft Edge:
- To access the menu, launch Microsoft Edge and click the three dots in the upper right corner of the screen.
- After swiping down, choose “Settings.”
- Continue swiping down to select “view advanced settings.”
- Select the “Manage” option under “Website Permission.”
- Select the toggle next to each dubious URL.
Manual Steps to Remove Trojan:Win32/Bamital.G
Remove Trojan:Win32/Bamital.G using Control-Panel:
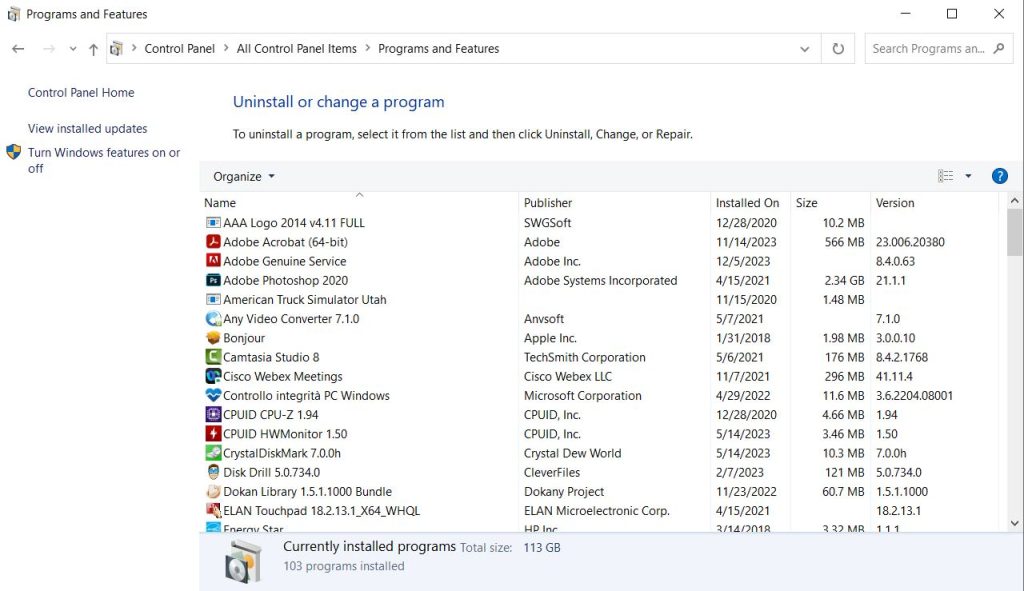
Windows 7:
- After selecting “Start,” choose “Control Panel.”
- Click “Uninstall Program” after finding “Programs.”
Windows XP:
- After selecting “Settings” from the “Start” menu, click “Control Panel.”
- Find and select the “Add or Remove Program” option.
- Now choose the programs you want to remove.
- Click on Remove.
Windows 10 and 8:
- Go to the main menu and choose “Control Panel”
- Now pick “Program and Features”
- Select the malicious programs you want to remove.
- Now hit the Remove button.
Remove Trojan:Win32/Bamital.G from Internet Browsers
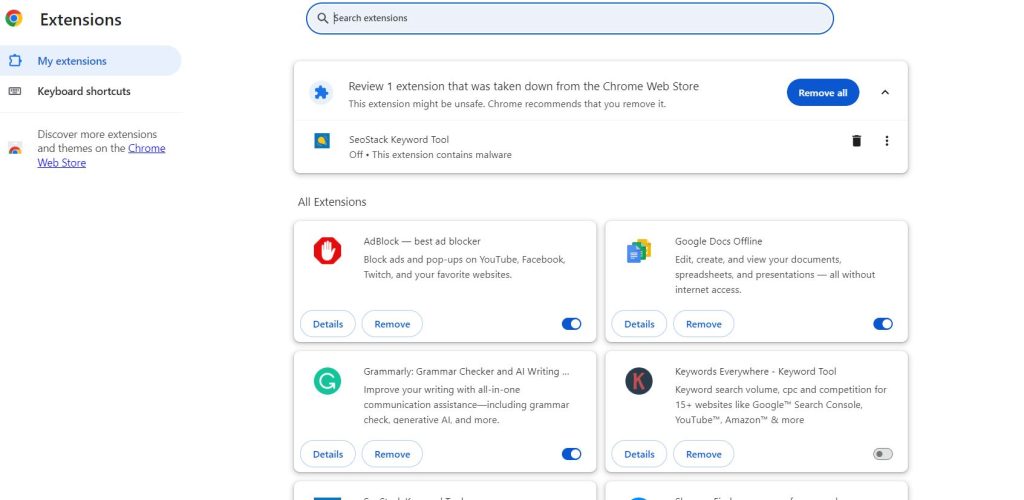
Remove from IE:
- Delete malicious extensions from IE
- In Internet Explorer, click the gear icon located in the upper right corner.
- Choose “Manage Add-ons.”
- Click “Remove” after searching for any recently installed add-ons or plug-ins.
Remove from Google Chrome:
- To access the Google Chrome menu, click the three vertical dots.
- Select “Extensions” after choosing “More tools.”
- All of the recently installed add-ons can be found and removed using a search.
Remove from Firefox Mozilla:
- Click the Firefox menu, and then choose “Add-ons.”
- Select “Extensions.”
- All recently installed browser plug-ins should be selected.
- Select the malicious extensions and select Remove.
Remove from Safari:
- Launch Safari; select “Preferences” from the “Menu” menu.
- Select all of the recently installed “Extensions” by clicking on the “Extension.”
- Select “Uninstall” from the menu.
Using Malwarebytes to get rid of unwanted programs and Trojan
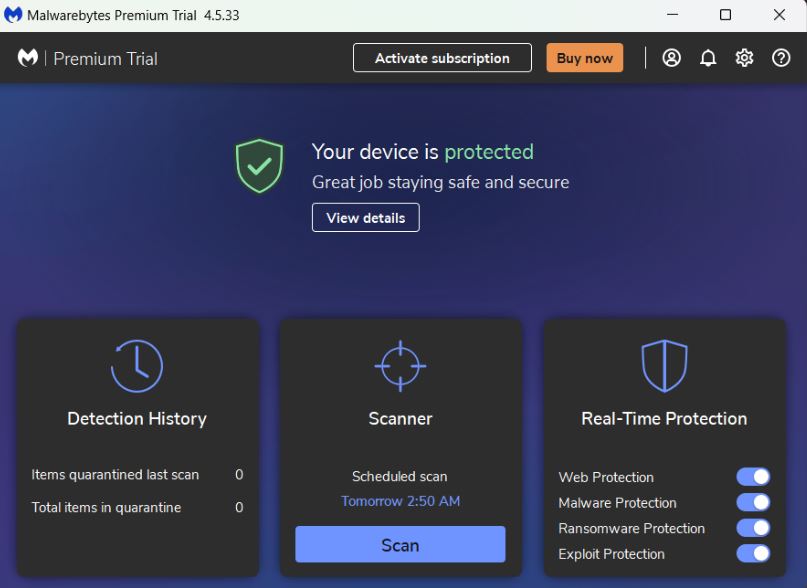
To detect and eliminate any infections, adware, or unwanted programs on your computer, we will now install Malwarebytes.
For good reason, Malwarebytes is among the most widely used and well-liked anti-malware programs for Windows.
It won’t cost you a dime and can remove a wide variety of malware that other programs frequently overlook.
Malwarebytes is a valuable tool in the battle against malware, and it is always free to use for removing infections from infected devices.
- Download the Malwarebytes.
- Double-click the setup file for Malwarebytes.
- Double-clicking the MBSetup file will launch Malwarebytes onto your PC after the download is complete.
- Now that Malwarebytes is installed on your computer, click the “Scan” button to begin a scan.
- Malwarebytes will begin scanning your computer for malicious software and automatically update the antivirus database.
- Now, Malwarebytes will search your computer for malware, including browser hijackers.
- A screen displaying any malware, adware, or potentially unwanted programs found by Malwarebytes will appear after the scan is complete.
- Click the “Quarantine” button to eliminate the malware that Malwarebytes has identified, including the adware.
- At this point, Malwarebytes will eliminate every malicious file and registry key it has discovered.
- Malwarebytes may ask you to restart your computer to finish the malware removal process.
Using HitmanPro to Remove Malware
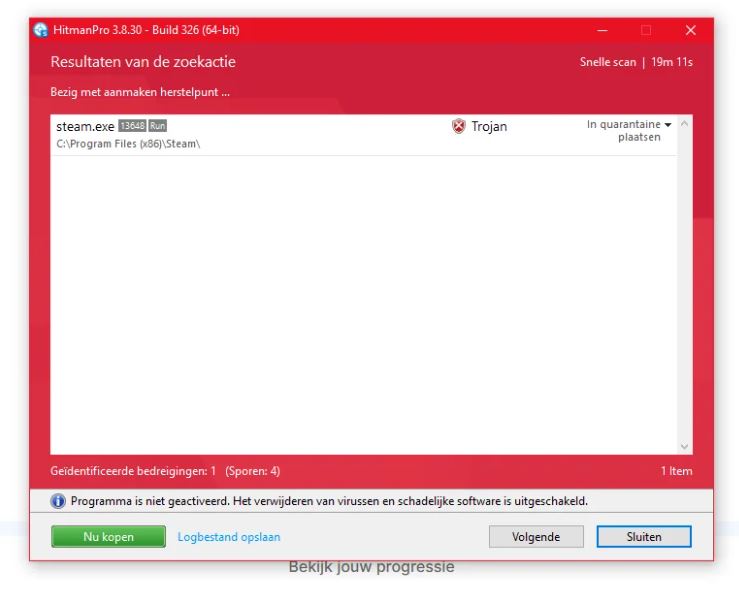
Here, we will download HitmanPro and use it to perform a scan to get rid of Trojan horses, rootkits, and other dangerous software while the computer is operating normally.
HitmanPro is a second-opinion scanner that employs a novel cloud-based method for detecting malware.
HitmanPro looks for unusual activity in files in places where malware typically resides as well as in the behavior of active files.
- Download the HitmanPro.
- Install HitmanPro in your system.
- HitmanPro will now start looking for malicious software on your computer.
- HitmanPro will show a list of all the malware it has discovered after the scan is complete.
- Now remove the items it has detected, click the “Next” button.
- The status of the different programs that were removed will be displayed on a screen that appears once the malware removal process is finished.
- After selecting the Next button, you should select the Reboot button if prompted.
Using AdwCleaner
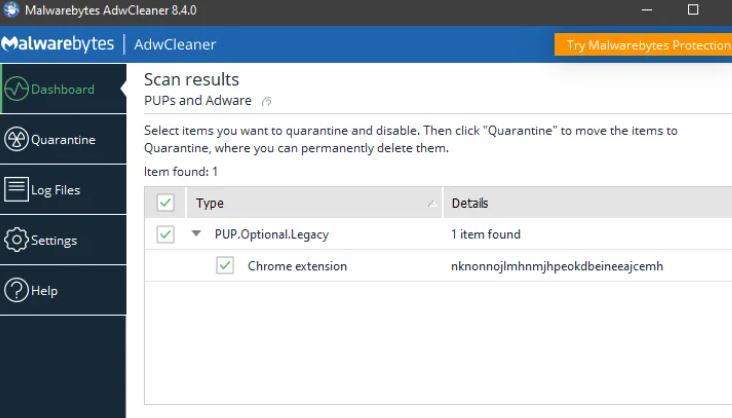
AdwCleaner will be utilized to eliminate undesired browser extensions and malicious browser policies from your computer.
Popular on-demand scanner AdwCleaner is free and effective at removing malware that is missed by even the best anti-virus and anti-malware programs.
It comes with very handy tools such as an on-demand scanner that can be used to address adware’s side effects, Malware, including browser hijackers.
- Get AdwCleaner.
- Click the setup file twice.
- After installation is finished, select “Dashboard” and then “Scan” to initiate a computer scan.
- AdwCleaner will now perform a malware scan on your computer. A few minutes may pass during this process.
- AdwCleaner will show every item it has found when the scan is finished.
- To eliminate the malicious software from your computer, click the “Quarantine” button.
- To get rid of the malicious programs, click “Continue.”
- Now, AdwCleaner will remove every piece of malware it finds from your computer.
- You could be prompted to restart your computer after the malware removal procedure is finished.
Conclusion
It is essential to only download software from reliable sources and to completely avoid using untrusted programs.
Users should do extensive research on any program and read reviews from reliable sources before downloading it.
To learn more about any software that might raise red flags, it is also a good idea to check anti-malware message boards.
Ultimately, being cautious and refraining from downloading software from unreliable sources is the best defence against Trojan attacks.

It’s me Mosaab, the founder and leading author of MalwareYeti.com. Over the years, I have gained a lot of experience when it comes down to building or fixing computers. Throughout my journey, I’ve built gaming PCs, fixed irritating Windows errors, and removed sticky malware/viruses that have affected machines. You can learn more about me on our About us page.

