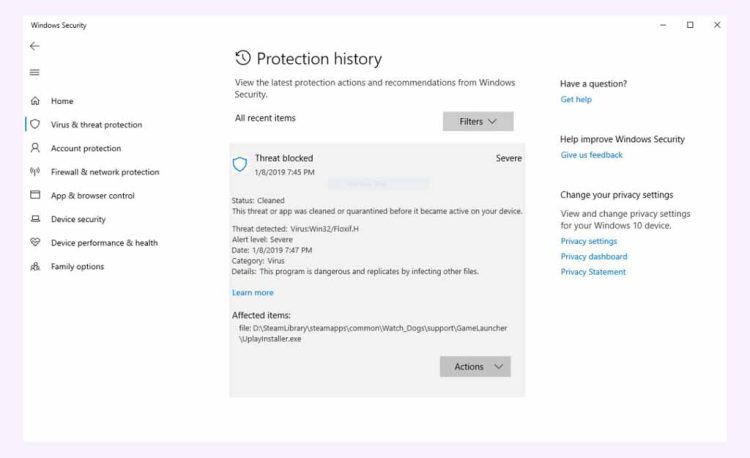
You may have found this virus threat from Windows Defender by receiving an alert stating that it had identified the particular malware on your system.
These detections are Windows alarm signals alerting you to potentially dangerous content.
It is important that you take the necessary measures to protect your device and never ignore any alerts that suggest you have a dangerous virus on your system.
These threats are often acquired by clicking on emails, visiting malicious websites, or receiving spam emails.
Virus: Win32/Floxif.H will start to propagate throughout your PC through Windows System files as soon as it is installed.
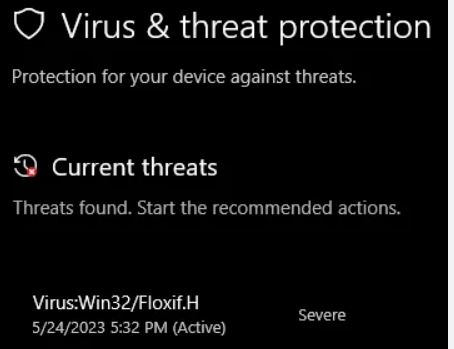
What is Win32/Floxif.H Virus?
Floxif.H is a malware that targets Windows executables and DLL files. Once infected with Floxif, the infected data can monitor activities on the device and act as a way in for other malware.
The following are the most common symptoms experienced by users whose devices have been infected with Virus: Win32/Floxif.H.
- Unexpected issues with internet access and applications
- The computer freezes or slows down
- Difficulties opening or finding documents or files.
- Unusual pop-up ads appear while online or browsing.
- Overheating and excessive CPU usage.
These types of detections are very dangerous because they can be used to attack other online users by stealing their privacy credentials, financial information, and other sensitive information.
If you believe you have been infected with this virus, it is critical that you remove it as soon as possible.
Typically, Windows Defender would have been sufficient to remove the threat. Unless certain circumstances prevent Windows Defender from removing the malware, you can use Malwarebytes Anti-malware to do so.
Sources of the infection:
- Infected files are shared through messaging platforms.
- Infected files downloaded from cloud storage or online repositories.
- Other types of virus strains employ Floxif in their activities.
- Malicious scripts on infected websites that make malware download automatically onto your device as soon as the page loads.
- Peer-to-peer sharing of infected files.
- Infected external devices, such as hard drives or USB sticks.
How Win32/Floxif.H Enter my System?
The main goal of the Floxif Trojan is to remain undetected on your computer. The Trojan infiltrated computers through a corrupted version of CCleaner. It affects your system just like the Trojan:Win32/Wacatac.B!ml virus.
Another scenario for getting this Trojan occurs when you open various types of e-mail attachments, the most common of which are fake invoices, receipts, and other documents of various types.
Your computer may start to see the following activities from the Floxif Trojan:
- Disable antivirus protection.
- Disable Windows Firewall.
- Influence the Windows operating system.
- Take screenshots.
- Log keystrokes on your computer.
- Obtain saved passwords.
- Escalate privileges.
- Read & write files.
- Delete files.
- Record audio.
- Tap into your camera.
- Control all connected devices.
- Update itself.
- Install additional viruses on the compromised system.
How to Remove Win32/Floxif.H
We strongly advise you to read the instructions below in order to remove the Floxif Trojan.
They were created to assist you in using the information in this article in conjunction with the steps to delete Floxif.H virus.
It is strongly advised to use advanced anti-malware software for removal for maximum effectiveness and future protection, as well as for faster removal.
Scanning your computer with such software is a good idea because it will save you a lot of manual removal time while also protecting your system from future threats.
Method 1: Removal Steps For Windows OS:
1. Stop the malicious process that Win32/Floxif.H and related malware are running:
- Press the Ctrl, Shift, and Esc keys simultaneously to start Windows Task Manager
- Locate any malware or malicious process connected to Win32/Floxif.H, then right-click on it to select End Process.
2. Delete any malicious software associated with the Win32/Floxif.H virus:
- To access the Run screen, simultaneously press the “Win + R” keys.
- Type “Control Panel” into the Run window and click the OK button.
- Click Programs in the Control Panel and choose Uninstall a program.
- Search for any malicious software associated with the Win32/Floxif.H virus.
- Right-click on the malicious software and select Uninstall.
3. Delete the extension installed by Win32/Floxif.H and related malware.
- Chrome
- Microsoft Edge
- Firefox
- Microsoft Internet Explorer
On Chrome:
- Select Extensions by clicking Tools from the Chrome menu:
- Find an extension that is related to Virus: Win32/Floxif.H threat, Now Click the Trash can icon to delete them.
On Microsoft Edge:
- Open Microsoft Edge and select Extensions by clicking the More button in the lower right corner.
- Click Remove after selecting the extensions you wish to delete
On Firefox:
- Select Add-ons from the menu bar. The Add-ons Manager window will appear.
- In the Add-ons Manager tab, navigate to the Extensions panel and search for extensions that may be associated with Virus: Win32/Floxif.H threat. Now Click the Remove button.
On Internet Explorer:
- Start Internet Explorer, and then select Tools, then Manage Add-ons.
- Select Toolbars and Extensions on the left side of the window, and then locate an extension that may be associated with Virus: Win32/Floxif.H or another potential threat, and then click the Disable button.
4. Remove malicious files created by Virus: Win32/Floxif.H or related malware.
- To open the Run window, press the Windows and R keys simultaneously. Type the regedit key and select OK.
- To begin a search for a virus, type its name into the Find window of the Registry Editor by pressing the Windows key and the F key simultaneously.
- When the search is done, right-click the folders related to Virus:Win32/Floxif.H and click the Delete button
5. Reset Web Browsers to remove Hijackers Brought by Virus: Win32/Floxif.H.
Reset Chrome:
- Select the Chrome menu button.
- Choose Settings.
- Then, in the Settings screen, select the “Advanced”.
- Now Select “Reset” settings to their “original defaults” from the menu.
- When the confirmation dialogue box shows up, select “Reset Settings.”
Reset Microsoft Edge:
- Select the Microsoft Edge primary menu button.
- When the drop-down menu displays, select the “Settings” button.
- Tap on “Reset Settings”
- Click on “Restore settings to their default values”
- In the newly opened confirmation window, select the “Reset” button”.
Reset Firefox:
- Click on the Firefox menu button
- Click on the “Help“ button when the drop-down menu appears
- Select “Troubleshooting Information“ from the Help menu
- Now hit the “Refresh Firefox” button.
- Please confirm in the newly opened window, Click on “Refresh Firefox” to finish the reset.
Reset IE:
- Click on “Internet Options” after opening Internet Explorer.
- Choose the “Advanced” tab, and click on the “Reset” button
- Now, pick the “Delete personal settings” checkbox, and click on the “Reset” button.
Method 2: Using Malwarebytes Anti-Malware:
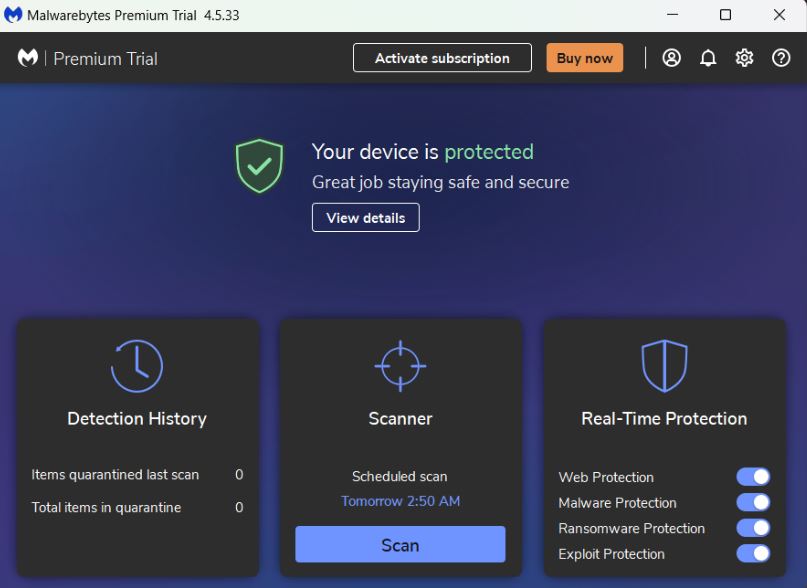
The instructions listed below can be used to use Malwarebytes to eliminate harmful threats from the computer:
1. Download Malwarebytes Anti-Malware
2. Go to their download page and initiate a Free Download to get the program started on your PC.
3. Open the executable file in File Explorer after the Malwarebytes setup file has finished downloading.
4. Then, right-click the setup and choose “Run as administrator” to allow the highest level of system authority and ensure Malwarebytes is installed correctly.
5. Pay close attention to the directions provided by the installation setup wizard and enter all necessary information.
6. Select the scan tab and start a system scan from the application’s home screen.
This will perform a comprehensive system scan, encompassing the memory, startup items, registry, and file system.
7. Malwarebytes will display the harmful viruses and threats found on your computer after the scan is complete.
8. Choose every file that has been identified as malicious from the report and press the quarantine button to remove the malicious files from the computer.
9. To complete the entire system scan process, the program might ask you to restart the computer after quarantining the virus files.
Ensuring the complete removal of malware files requires more than just quarantining them.
There is a widespread misperception that everything is gone as soon as the quarantine button is clicked.
The malware is still present in the system; it is just contained in the quarantine folders of the anti-malware program, even though its negative effects and malicious activities have stopped.
Go to Detection History from the home screen, select all Quarantined items, and then click Delete to remove it entirely from the computer.
Conclusion
Always ensure that the device you are using has protection from sneaky cyberattacks and smart attacks.
Having a strong line of defence is critical to ensuring the safety of your computer system and information,
even though performing preventative measures and staying away from questionable websites are important as well.

It’s me Mosaab, the founder and leading author of MalwareYeti.com. Over the years, I have gained a lot of experience when it comes down to building or fixing computers. Throughout my journey, I’ve built gaming PCs, fixed irritating Windows errors, and removed sticky malware/viruses that have affected machines. You can learn more about me on our About us page.