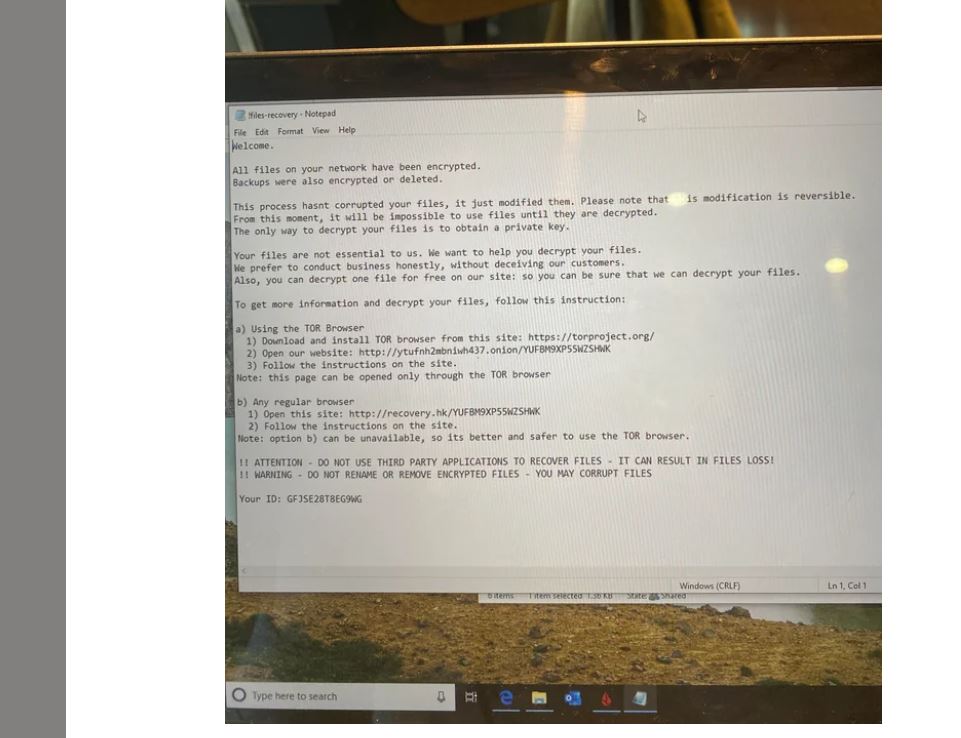
Ransomware is a kind of malware that encrypts the files of a victim. The attacker then seeks a ransom from the target in exchange for restoring access to the data.
Ransomware attackers typically demand money in exchange for a decryption key to unlock personal files.
The victims are given payment instructions, and the cost can range from a few hundred to thousands of dollars.
Payments are typically made in Bitcoin, which is the preferred currency of many cybercriminals.
Ransomware can target personal files such as documents, databases, source codes, pictures, videos, and more.
How Ransomware Attackers Work?
There are several methods by which attackers select which organizations to target with ransomware.
It’s sometimes a matter of opportunity for example, attackers may target universities because they have smaller security teams and a diverse user base that engages in a lot of file sharing, making it easier to breach their defenses.

However, some companies make attractive targets because they appear to have a higher likelihood of speedily fulfilling a ransom payment.
Governmental organizations and healthcare facilities, for example, frequently require instant access to their records.
Law firms and other businesses that handle sensitive data might be more open to paying to conceal information about a breach, and they might be more vulnerable to leakware attacks.
Types of Ransomware
There are two general types of ransomware:
- Encrypting or crypto-ransomware
- Non-encrypting or screen-locking ransomware
1. Encrypting or Crypto-Ransomware
The most prevalent kind, known as crypto-ransomware or encrypting ransomware, encrypts the victim’s data and holds it captive.
After that, the attacker offers to provide the encryption key required to decrypt the data in return for a ransom.
2. Non-Encrypting or Screen-Locking Ransomware
Non-encrypting or screen-locking ransomware is a less frequent type of malware that locks the entire device of the victim by preventing access to the operating system.
The device shows a screen that demands a ransom instead of booting up normally.
These two types are further subdivided into the following categories:
Leakware:
Ransomware that steals or exfiltrates private information and makes threats to make it public is known as leakware.
Today’s variants of leakware frequently do both encryption and data theft, unlike their predecessors.
Mobile ransomware:
Mobile ransomware, which affects mobile devices, is typically distributed via malicious apps or drive-by downloads.
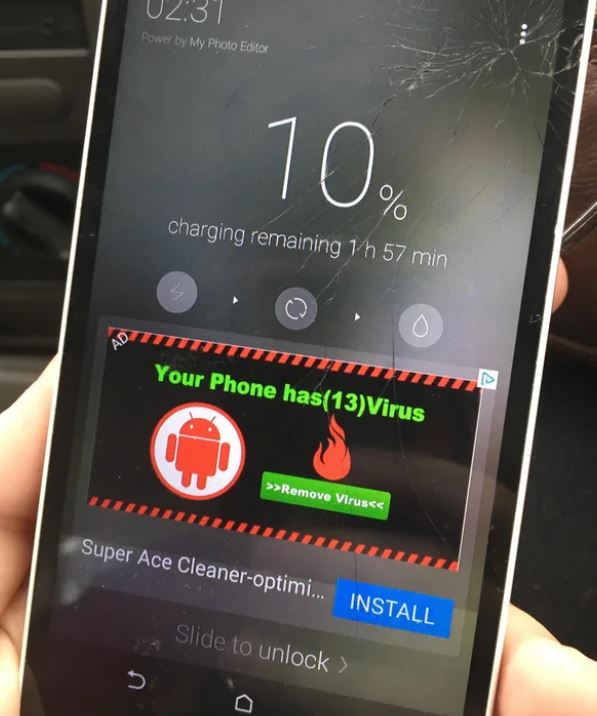
Mobile ransomware is typically non-encrypting ransomware because most mobile devices have automated cloud data backups. This makes reversing encryption attacks effortless.
Wiper Ransomware:
Wiper Ransomware is a kind of malicious software that threatens to delete all data on a computer or network if a ransom is not paid.
However, in some cases, even after the ransom is paid, the ransomware destroys the data.
This type of wiper is typically used by nation-state actors or hacktivists rather than common cybercriminals.
Scareware is simply ransomware designed to intimidate users into paying a ransom.
This can mimic an authentic virus infection alert and urge the victim to buy antivirus or antimalware software.
It can also pose as a message from a law enforcement agency, accusing the victim of a crime and demanding a fine.
Scareware can sometimes be ransomware, locking the device or encrypting the data; other times,
it can be the ransomware vector, which encrypts nothing but forces the victim to download ransomware.
Stages of a Ransomware Attack
Typically, a ransomware attack goes through the following phases.
Stage 1:
Phishing and vulnerability exploitation are two of the most common access vectors for ransomware attacks.
Stage 2:
This second stage may involve an intermediary remote access tool or malware before establishing interactive access, depending on the initial access vector.
Stage 3:
In this third phase of the attack, the attackers concentrate on learning about the local system and domain they currently possess and on breaking into other systems and domains.
Stage 4:
Here, the goal of ransomware operators is to locate important data and extract it, usually by exporting or downloading a copy for personal use.
Attackers may steal any information they can get their hands on, but they typically target particularly valuable information such as login passwords,
sensitive consumer data, and intellectual property that they can utilize to commit double-extortion.
Stage 5:
Crypto ransomware begins to recognize and encrypt files. To increase the pressure on the victim to pay for the decryption key, some crypto ransomware disables system restore features or deletes or encrypts backups on the victim’s computer.
Non-encrypting ransomware locks the device’s screen, floods it with pop-ups, or otherwise prevents the victim from using it.
Once the files have been encrypted and the device has been disabled, the ransomware informs the victim of the infection, usually through a.txt file on the computer’s desktop or a pop-up notification.
The ransom note includes instructions for paying the ransom, which is usually done with cryptocurrency or another untraceable method, in exchange for a decryption key.
Steps to Prevent Ransomware Attacks
No matter how well-prepared and hygienic security measures are, ransomware attacks will never completely bypass them.
It is now imperative to identify the attack as soon as possible and stop it from propagating to additional devices and systems.
1. Isolate the infected device:
Disconnect any wired or wireless connections to the internet, networks, mobile devices, flash drives, external hard drives, cloud storage accounts, and network drives as soon as possible from the impacted device.
By doing this, ransomware will be kept from infecting additional devices.
2. Understand the type of ransomware:
Helping with the removal process can be provided by knowing which ransomware strain infected the device.
This might not be feasible if device access is restricted, as in the case of locker ransomware.
To determine whether the compromised device is infected, an experienced security specialist may need to examine it or use software tools.
While some tools can be downloaded for free, others call for a subscription that costs money.
3. Remove the ransomware:
The ransomware needs to be eliminated before the system can be restored.
Ransomware software infects a system, encrypts its files, and/or locks down system access during the initial hack.
The restriction can only be unlocked or decrypted using a password or decryption key.
There are several ways to get rid of ransomware:
Use Malwarebytes:
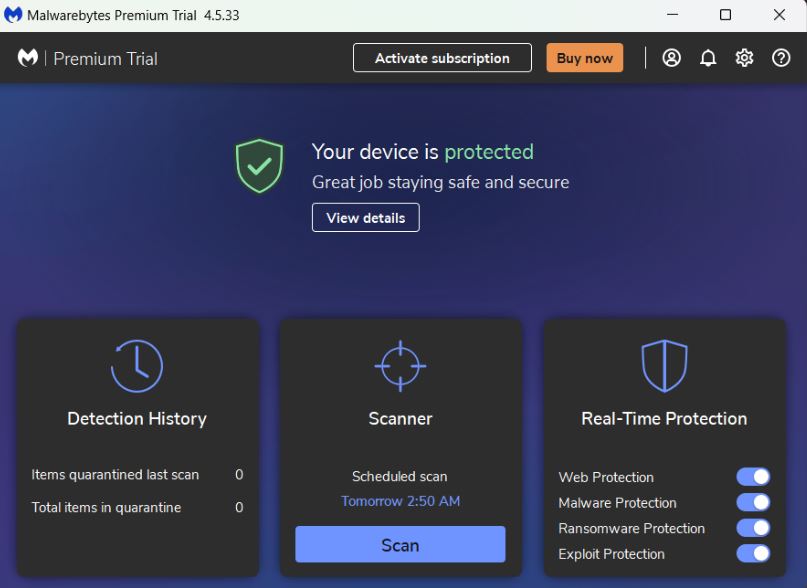
To check for and eliminate any infections, adware, or unwanted programs that might be on your computer, we will install Malwarebytes.
- Download Malwarebytes on your Windows computer.
- Double-click the setup file for Malwarebytes.
- To install Malwarebytes, follow the instructions on the screen.
- After Malwarebytes has finished installing.
- Select “Scan” from the menu.
- Now, Malwarebytes will search your computer for malware, including browser hijackers.
- A screen displaying any malware, adware, or potentially unwanted programs found by Malwarebytes will appear after the scan is complete.
- Click the “Quarantine” button to get rid of the malware that Malwarebytes has identified, including the adware.
- At this point, Malwarebytes will eliminate every malicious file and registry key it discovered.
- Malwarebytes may ask you to restart your computer to finish the malware removal process.
Use AdwCleaner:
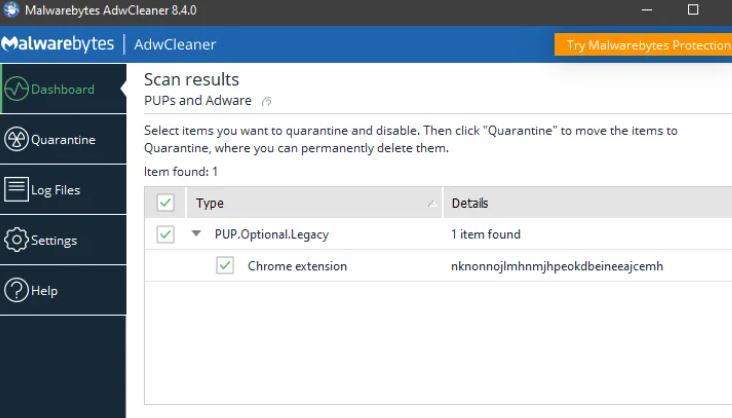
We will now use AdwCleaner to clean your computer of unwanted browser extensions and malicious browser policies.
- Get AdwCleaner.
- Click the setup file.
- Click “Settings” on the left side of the window after AdwCleaner launches, and then select “Reset Chrome policies.”
- To run a computer scan, click “Scan” after selecting “Dashboard” on the left side of the AdwCleaner window.
- AdwCleaner will now perform a malware scan on your computer.
- All of the items that AdwCleaner has found will be displayed once the scan is finished.
- To eliminate the malicious software from your computer, click the “Quarantine” button.
- Now that the program has to close any open programs before it can begin cleaning, AdwCleaner will ask you to save any open files or data.
- Press the “Continue” button to ensure the removal is completed.
- Now, AdwCleaner will remove every piece of malware it finds from your computer.
- You could be prompted to restart your computer after the malware removal procedure is finished.
Use EaseUS Data Recovery Wizard:
With a few clicks, EaseUS Data Recovery Wizard can restore and repair corrupted files.
Its robust scanning algorithms are capable of locating and retrieving vast file-type libraries, encompassing all of the widely used document, audio, video, and photo formats.
- Get the free version of EaseUS Data Recovery Wizard.
- Double-click the setup file for EaseUS Data Recovery Wizard Free.
- Install the EaseUS Data Recovery Wizard by following the on-screen instructions.
- Click “Start Now” to launch the EaseUS Data Recovery Wizard after the installation is finished.
- Click “Scan” after selecting the drive or folder containing the encrypted files you wish to recover.
- Await the completion of the EaseUS Data Recovery Wizard scan.
- Find the files that require recovery.
- The files that can be recovered are displayed on a screen that appears once the EaseUS Data Recovery Wizard scan is complete.
- To view a complete preview of a file, double-click on it or click the “Preview” button.
- In the end, pick the files you wish to retrieve and press, “Recover.” Select a secure location to store each file.
Conclusion
If your computer becomes infected with a family of ransomware that is extremely dangerous, it could lead to multiple attacks on the workstation.
It is still advised to take some extra safety precautions, though.
Patching and securing Remote Desktop Protocol servers with virtual private networks that support multi-factor authentication is essential first.
This will lessen the chance of breaches and unwanted access.
Organizations must also be on the lookout for phishing attempts, especially as they transition to remote work environments.

It’s me Mosaab, the founder and leading author of MalwareYeti.com. Over the years, I have gained a lot of experience when it comes down to building or fixing computers. Throughout my journey, I’ve built gaming PCs, fixed irritating Windows errors, and removed sticky malware/viruses that have affected machines. You can learn more about me on our About us page.