Phishing is an attempt to deceive the victim into granting permission for the attacker to do anything they want, such as reveal bank account information, login credentials for a system, or other personal information.
In social engineering, phishing involves psychological manipulation and deception, where threat actors disguise as trustworthy entities to trick users into taking specific actions.
Providing personal information, downloading and installing dangerous files, and following links to phoney websites are a few of the activities that are involved.
What Does a Phishing Email look like?
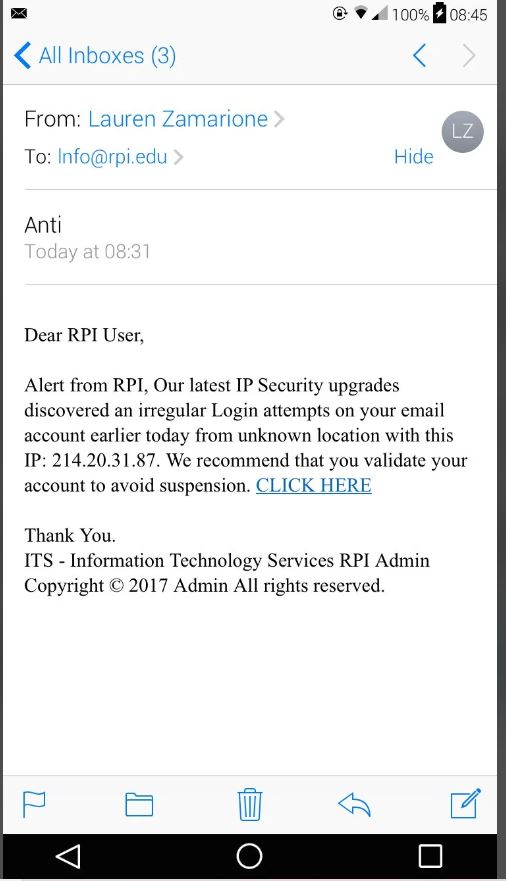
Phishing emails are so sinister because they look legitimate. Usually, phishing emails have these characteristics in common that should make you suspicious:
- Attachments or links
- Spelling errors
- Poor grammar
- Unprofessional graphics
- There is an unnecessary urgency about verifying your email address or other personal information immediately.
- Generic greetings like “Dear Customer” instead of your name.
How Phishing Works?
A phishing campaign starts by sending a malicious message. An attack disguises itself as a message from a legitimate company. The more the message looks like the real company, the more likely an attacker will succeed. The main goal of attackers is to steal personal information or credentials.
When someone sends an urgent message, they might lose their account, money, or job. Users don’t stop to think if the demands are reasonable or if the source is legitimate.
Phishing keeps changing to get around security and catch people, so companies must keep teaching their workers how to recognize the latest ways of phishing. Phishing can lead to a serious data breach if one person falls for it.
That’s why it’s one of the most important threats to mitigate and the hardest because it requires human defences.
Types of Phishing Attacks
Understanding what to expect from phishing is the initial obstacle it may be sent through a variety of channels, including messages, phone calls, and even hacked URLs on reputable websites.
You get a better grasp on phishing when you see it in action. You might have already encountered a few of these rip-offs and tossed them in the trash as junk mail.
Most people are likely to experience at least one of these forms of phishing, regardless of how they are targeted.
1. Email Phishing:
Email is the preferred method of transmission for phishing attacks. The criminals typically register forged domain names that imitate legitimate entities known as spoofing to send countless requests to their targets.
For fake domains, attackers can add or replace characters, or use the trusted organization’s name as the email username.
Many phishing emails employ a sense of urgency or a threat to get people to act quickly, without checking the origin or authenticity of the message.
- There are several goals to email phishing messages.
- Inducing the user to click a link to a malicious website to install malware on their device.
- The user is prompted to download an infected file, which is then used to spread malware.
- The user is prompted to click on a link to a fake website and provide personal information.
- Requiring the user to respond and provide personal information.
- Email Phishers use a variety of techniques to make their attacks look more believable to their targets and to achieve their goals. Some common email phishing techniques include:
Social Engineering:
Psychological deception is used to take advantage of the people who are targeted by phishing attacks. A phisher may employ deceitful methods, enforcement, bribery, or other techniques to achieve their goal.
Typosquatting:
Phishers may use domains and URLs that look like legitimate, trusted ones. If the target isn’t paying enough attention, they may think the link is legit.
Email Spoofing:
The recipient’s trustworthiness is reflected in the display name of a spoofed email. The sender’s name in an email is a simple text field that falls under the sender’s control. Phishers exploit this fact to disguise emails as coming from reputable email accounts.
URL Shortening:
Phishers normally use link shorteners to cancel the URL target destination to trick the users into clicking on the phishing page.
Malicious Redirects:
Redirects are used to redirect a browser to another page if the original URL is unavailable, incorrect, or outdated. Malicious redirects can be used to send users to a phishing page instead of a legitimate one.
Hidden Links:
Some links can be hidden in text or images. If a user accidentally clicks the hidden link, they will be taken to a phishing page.
2. Spear Phishing:
Cybercriminals use spoofed email as bait for Phishing, while Spear Phishing involves attackers picking their targets.
A spear-phishing attack targets a single organization or a small group of businesses instead of multiple login credentials.
Spear-phishing is used to target countries for sensitive information via fraudulent emails, for instance, a government agent from one nation may target another country for sensitive information via fraudulent emails.
Typically, the perpetrator possesses a portion or all of the ensuing details regarding the victim.
- Name
- Place of employment
- Job title
- Email address
- Specific information about their job role
3. Whaling:
Senior management and other high-profile positions are targeted by whaling attacks. Whaling has the same end goal as other phishing tactics, but the approach is often ethereal.
A lot of information in the public domain can be used to craft incredibly effective attacks by senior employees.
These attacks typically don’t employ tricks like shady web addresses and forged hyperlinks.
Instead, they send highly individualized messages based on the details they uncover during their investigation into the victim.
False tax returns are used by whaling attackers to uncover private information about the victim and use it to craft their attack.
4. Smishing and Vishing:
This is a scam that uses the phone instead of written communications. Smishing is sending fake SMS messages and vishing is calling people.
In a common scam called voice phishing, someone pretends to work for a credit card company or bank and tells people their account has been hacked.
Criminals ask the victim to give them their payment card information, so they can verify their identity or transfer money to a secure account.
Vishing scams can also involve making automated phone calls that pretend to be from a trusted company and asking the person to type their personal information on their phone’s keyboard.
5. Angler Phishing:
Fake accounts belonging to well-known entities are used in these attacks. An account handle that appears to be a genuine organization and the same profile picture is used by the attacker.
Attackers take advantage of consumers’ tendency to make complaints and request assistance from brands using social media channels to take advantage of consumers.
The individual instead of contacting the genuine brand, contacts the fictitious social profile of the attacker.
When they get such a request, they may ask the customer for personal information, so they can figure out the problem and respond appropriately.
Other times, the attacker links to a fictitious customer assistance page, which in reality is a hacked website.
Most Targeted Industries Under Phishing Attacks
Since financial gain is the major motivation behind most phishing attacks, attackers typically target particular companies that either hold credit card data or have the resources to make significant payments.
The following are the major industries that are targeted:
- Online stores
- Social media
- Banks and other financial institutes
- Payment systems
- IT companies
- Telecommunication companies
- Delivery companies
How to Prevent Phishing Attacks (Working Strategies)
Recognizing the dangers associated with phishing attempts and a few common justifications is the first step toward stopping them.
Considering how sophisticated phishing attempts are these days, someone will probably fall for one.
You shouldn’t give out your credit card info unless you’re 100% confident in the site you’re visiting.
If you’re going to share your data, make sure you check the legitimacy of the website, the legitimacy of the company, and the safety of the website itself.
Additionally to these precautions, the top strategies for shielding your data and systems from phishing assaults are listed below:
1. Recognize the Signs of Phishing Scams:
New phishing attack methods are being developed all the time, but they all share commonalities that can be identified if you know what to look for.
You can find many sites online that keep you up to date on the latest phishing attacks and key identifiers.
Regular security awareness training can help you avoid a potential attack by sharing the latest attack methods with your users.
2. Free Anti-Phishing Add-Ons:
These days, the majority of browsers allow you to download add-ons like Netcraft that identify obvious signs of a dangerous website or warn you about well-known phishing websites.
There’s no excuse not to have this loaded on every device in your company they are often entirely free.
3. Security Awareness Training:
Security awareness training is important to prevent phishing attacks. This training should educate employees on the harm of phishing and teach them how to spot and report suspicious attempts.
Simulated phishing attempts can help organizations assess their own risk and make their workers more resilient.
When employees click on simulated phishing emails, it is important to tell them about the risks and remind them how to report suspicious emails.
Organizations may concentrate on enhancing security protocols, fortifying training, and expanding anti-phishing methods by keeping an eye on the outcomes of these initiatives.
4. Use Strong Passwords & Two-Factor Authentication:
Use complex passwords for all accounts and don’t share passwords. Use two-factor authentication whenever you can.
This makes things more secure by requiring a second check to make sure everything is okay.
5. Update Your System:
It can be annoying to get many updates and it’s easy to ignore them. Avoid this. Security patches and updates are released for a reason, most often to keep up with modern cyber-attack methods by patching holes in security.
If you don’t update your browser, you might get hacked because of bugs that could have been fixed easily.
6. Stay Cautious with Emails and Malicious Links:
Be careful when opening emails or clicking on malicious links. Don’t download attachments unless you know they’re important and from a reliable source.
It’s usually not a good idea to click on a link in an email or instant message. The minimum you should be doing is hovering over the link to see if the destination is the right one.
Some phishing attacks look like a copy of the real site, set up to record keystrokes or steal login/credit card information.
If you can go directly to the website by using your search engine instead of clicking on the link, then do so.
7. Avoid Unsecure Websites:
If the website’s URL doesn’t start with “https” or you can’t see a padlock icon next to it, don’t enter any sensitive information or download files from that website.
Sites without security certificates may not be designed for phishing scams, but it’s better to be safe than sorry.
8. Avoid Pop-Up Scams:
Not only are pop-ups annoying, but they are frequently connected to malware in phishing attempts.
You may now download and install free ad-blocking software on most browsers, which will automatically prevent the majority of dangerous pop-ups.
9. Regularly Change Your Passwords:
To stop an attacker from having unrestricted access to your online accounts, you should make it a practice to change your passwords frequently.
Your accounts may have been compromised without you knowing, therefore changing your passwords regularly can help to keep criminals out and avoid further attempts.
10. Use Anti-Phishing Tools:
Make use of anti-phishing techniques and technology that can identify and stop phoney emails and websites.
By putting up a barrier between your computer and the attacker, firewalls are a useful tool for preventing external assaults.
When used together, both desktop and network firewalls can improve your security and reduce the chances of a hacker infiltrating your environment.
Just like phishing attacks, you can also become a target of ransomware attacks, don’t forget to have a look at our guide here.
Conclusion
Training and awareness are important if firms want to stay ahead of cybercriminals. Learning about the various phishing attack types that attackers use can help you and your company avoid the negative effects of a cyberattack.
Knowing how phishing works and how it works will help you and your team spot warning signs in fake messages.
Organizations need to keep workers informed about the most recent phishing and social engineering tactics, with user-based awareness training being the most important line of protection.
Educating employees about upcoming threats lowers the chance and solidifies the firm’s dedication to cyber security.

It’s me Mosaab, the founder and leading author of MalwareYeti.com. Over the years, I have gained a lot of experience when it comes down to building or fixing computers. Throughout my journey, I’ve built gaming PCs, fixed irritating Windows errors, and removed sticky malware/viruses that have affected machines. You can learn more about me on our About us page.

